Personal Risk
The concept of risk has been an important one for me to consider in this industry. It is important to think of risk not just as “a thing that could happen” but as how likely said thing is to actually happen. We all do this subconsciously on a daily basis, if this weren’t the case then we would be perpetually paranoid and terrified about sudden tectonic shift or meteor strikes. In reality we are blasé about these dangers since we understand that the actual risk of such an event happening is tiny. The fact that we are largely powerless to do anything about such events may also play a part in this carefree attitude.
But what about the things we can control? Most of us are smart enough to look each way before crossing a road as we understand that not checking for cars will greatly increase the risk of being hit. Auto-mobiles are a technology that we have long grown accustomed to and few are blasé about the dangers and consequences of high speed collisions. Smart phones, on the other hand, have been around for a fair few years now and it seems that most people still don’t think to check whether or not their phone’s settings are causing any photos or videos they may take to be automatically uploaded onto a “cloud” storage server. Once that happens, once potentially deeply personal files exist on two systems as opposed to one, then the risk of them being stolen by malicious hackers effectively just doubled.
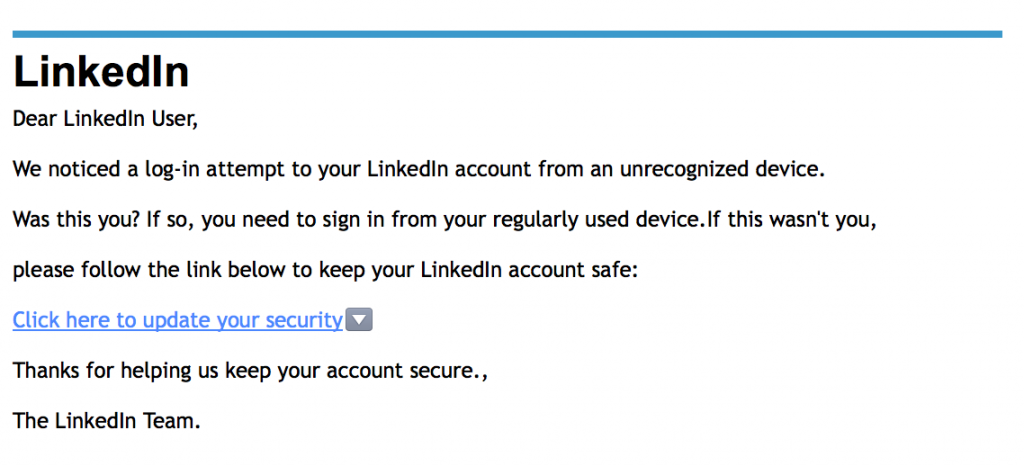
When discussing the matter of personal security with peers in a social setting I have found that a lax attitude is the norm. Common phrases are “What are the odds?”, “I’m not interesting enough to be targeted” or it’s immensely frustrating cousin “I’ve got nothing to hide”. How can someone know this if they don’t know what a hypothetical attacker is looking for? As we continue to embrace more and more technology into our daily lives and entwine it so tightly with social media then, as a whole, we really need to start thinking differently on these topics.
The odds really aren’t very good for us and it does sometimes seem to me that the reason many people think that they are, is because their heads are stuck ten years in the past as far as their awareness of attack methods go. Many a person has proudly announced to me that they don’t have any viruses because they have a firewall and they don’t click on suspicious emails and they don’t go on “dodgy” pornographic websites. This underlines a worrying lack of understanding when so many believe that their traffic management system is an infallible security measure. While the occasional and incredibly obvious scam email still does the rounds there are more advanced and complex phishing methods now, especially with the “rise of the app”. And the idea that only porn sites could be potential vectors for infection is very much an old fashioned one. Just the other day Malwarebytes announced via blog post that the Mail Online site was hit by an exploit that could infect vulnerable systems with ransomware. This is a website that boasts 156 million visits per month. There are so many attacks happening, all the time, and if you never think about your tech’s security, then the chances are you’re going to get hit or that you already have been.
-JG